
Clipboard Interceptors: How to Protect Your Cryptocurrency from Theft
Malware that attacks the clipboard has become a serious problem for cryptocurrency owners. Their main task is to imperceptibly replace crypto wallet addresses at the time of copying, directing your funds directly into the hands of fraudsters.
Signs of infection: How do you know if your clipboard is compromised?
Before moving on to preventive measures, it is important to determine if your computer has fallen victim to malware. Modern clipboard interceptors are extremely stealthy, so they can be difficult to detect.
Sophisticated Address Spoofing Techniques: A New Era of Spoofing
If earlier clipboard malware worked quite clumsily, simply replacing the address with a random wallet of the attacker, then the current generation of such programs acts much more cunningly. For example, a new type of malware known as Laplas Clipper uses cryptocurrency addresses that are very similar to the victim's intended recipient address. This means that even a careful check of the first and last characters of the address may not save you from deception.
Express system diagnostics: test yourself right now
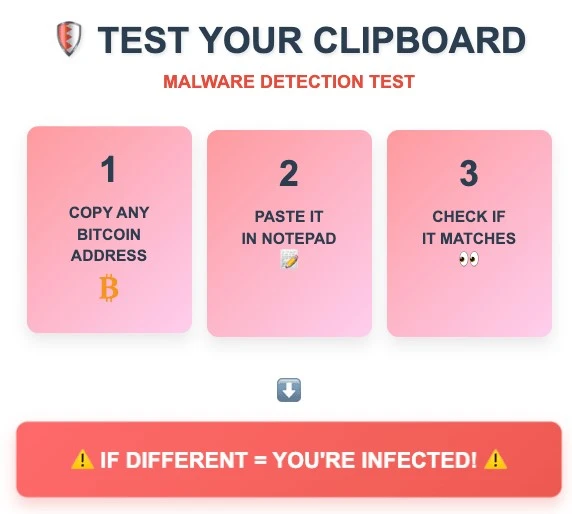
There is an easy way to quickly check your clipboard for compromise. To do this:
- Copy the following Bitcoin address: 12ECLtcbVvmUb3ob2YxJF5Ky2myd3UNG95
- Paste the copied address into any text editor (for example, Notepad).
- If the inserted address does not match the original one, your system is infected with clipboard malware.
It is also critical to analyze the history of your recent cryptocurrency transactions. Pay attention to any transactions sent to unknown addresses, especially if these addresses have similar start and end characters to the address of your intended recipient. This method of selection according to a template is a characteristic feature of modern interceptor programs.
Linked materials
Infection Routes: How Does Malware Get Into a System?
According to Binance, clipper malware is most often distributed through unofficial apps and plugins for Android devices. It is not uncommon for users to download such malware by accident, while searching for software in other languages, or through unofficial web resources used due to regional restrictions. Malware developers target users who need localized versions of programs or live in countries with restrictions on cryptocurrency transactions, as these groups are more likely to resort to downloads from unverified sources.
One of the most insidious ways of infection is the use of fake versions of legitimate cryptocurrency applications. For example, in February 2019, a fake version of the MetaMask crypto wallet was discovered on Google Play, which distributed the Clipper malware. Similar fake applications often have names that are almost identical to the original ones, making it difficult to recognize them without proper vigilance.
The scale of the spread of malware is really huge. According to AV-Test, there are over 1 billion malicious programs circulating on the Internet. More than half of them belong to the category of Trojan horses – malicious code disguised as harmless programs. This vast malware ecosystem means that the threat can come from the most unexpected places, including seemingly useful posts on forums or software repositories.

Implicit indicators in the system: what to pay attention to?
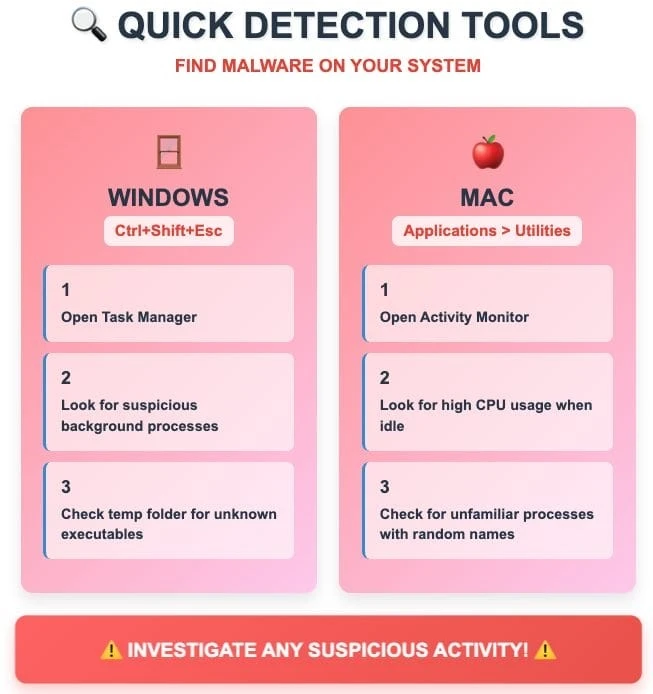
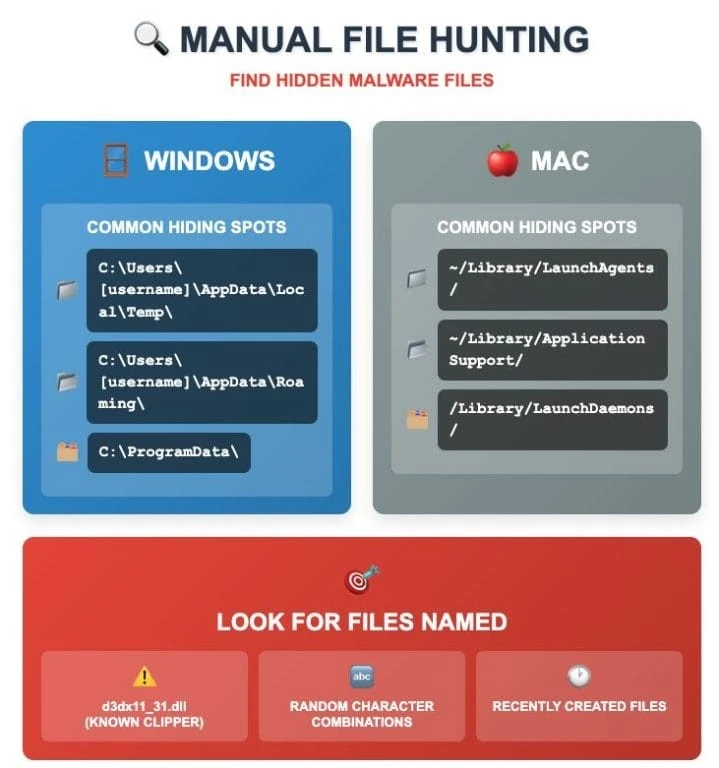
Modern clipboard interception programs are characterized by a high level of secrecy. Since they function in the background, showing no visible signs of their activity, it can be difficult to detect an infection. However, there are indirect signs that may indicate a problem. Check Windows Task Manager for suspicious processes, especially those that are actively using CPU resources when the computer is idle. Malware is often disguised as system processes with legitimate-sounding names. Look for recently created files in temporary folders, especially DLL files with names that resemble system components but were previously missing.
A startup entry named "DirectX 11" is a specific marker of some variants of clipboard-hijacking malware. When such software is installed, a DLL file named d3dx11_31.dll is downloaded to the Temp system folder and a "DirectX 11" entry is created to run it automatically when the user logs in.
Linked materials
Infection Prevention: How to Protect Your Crypto Assets?
Knowing the typical clipboard malware distribution paths is key to effective prevention. The cyberthreat landscape is constantly changing, and attackers are using increasingly sophisticated methods to deliver their code.
Threats to mobile platforms
According to a report by Binance, the main target of attacks using clipboard interceptors is mobile device users. This is because entering long wallet addresses on smartphones is even more inconvenient than on PCs, making copy-and-paste the most logical way to transfer addresses between apps. Android users are at increased risk, as "clipper" malware is often spread through Android apps and web app plugins. Such programs are usually downloaded from unofficial app stores or phishing sites. The openness of the Android ecosystem, despite its advantages in terms of functionality, creates loopholes for the distribution of malicious apps outside of the official Google Play Store.

Browser-based attack vectors
Another type of clipboard interception attack is carried out through websites or web applications. In this scenario, an attacker can inject malicious code directly into a web page. This code accesses the clipboard data on the user's computer when the user copies or pastes information from a given page. As such, simply visiting a compromised web resource potentially opens your clipboard for monitoring or manipulation. Browser security is becoming increasingly important as attackers actively target browser extensions and plugins. MetaMask, Coinbase, Phantom, Keplar, and other wallets may be at risk, as the StilachiRAT malware is capable of scanning the Google Chrome browser for cryptocurrency wallet extensions. It can then extract and decrypt the stored credentials to gain access to usernames and passwords.

Email attacks
Email remains one of the main vectors for infection. Cybercriminals often send out emails disguised as "urgent security updates" for popular crypto wallets or exchanges. Such messages usually create a false sense of urgency to make the user disregard standard precautions. Always go to the official website of the company yourself to check for information about any security updates, instead of clicking on links in suspicious emails.

Linked materials
Building Strong Protection Habits
Developing secure software download practices requires an understanding of the full range of threats. Always make sure to download the software from the developer's official website by entering the URL manually, and not by clicking on links from search results or email. Check the site's SSL certificate, pay attention to the official branding of the company and the availability of contact information.
For mobile users, the risks are particularly high. Use only the official app stores and be extremely careful with any programs that ask for unusual permissions, especially access to the clipboard. Carefully study app reviews and be suspicious of those that have few reviews or look like they are artificially created.

Ways to remove clipboard malware
At the slightest suspicion of infection, you must act immediately. Modern clipboard malware is capable of continuously running in the background, compromising your every cryptocurrency transaction.
Emergency Response Protocol
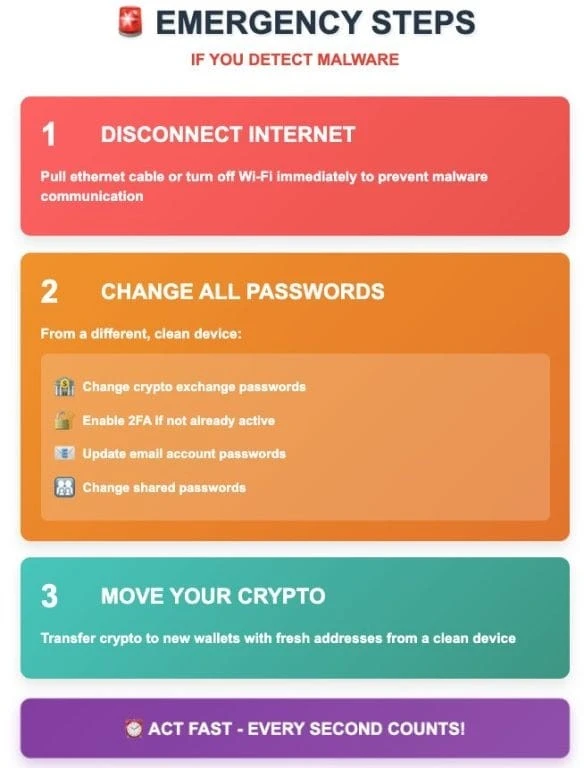
As soon as you suspect a malware infection, immediately disconnect your device from the internet. This will cut off the malware's communication with its C&C servers and stop a possible data leak. Information-harvesting Remote Access Trojans (RATs) can constantly monitor the contents of the clipboard in search of sensitive data, such as cryptocurrency wallet keys and passwords.
Using a completely different, guaranteed clean device, immediately change the passwords to all your cryptocurrency exchanges and activate two-factor authentication if it has not already been done. Create new wallet addresses and be ready to transfer your crypto assets to them. The key is to assume that any addresses you've copied recently may have been compromised.
 Binance BPlay Casino: How a Crypto Exchange Almost Became a Gambling Giant. But something went wrong.
Binance BPlay Casino: How a Crypto Exchange Almost Became a Gambling Giant. But something went wrong.Linked materials
Windows System Cleanup
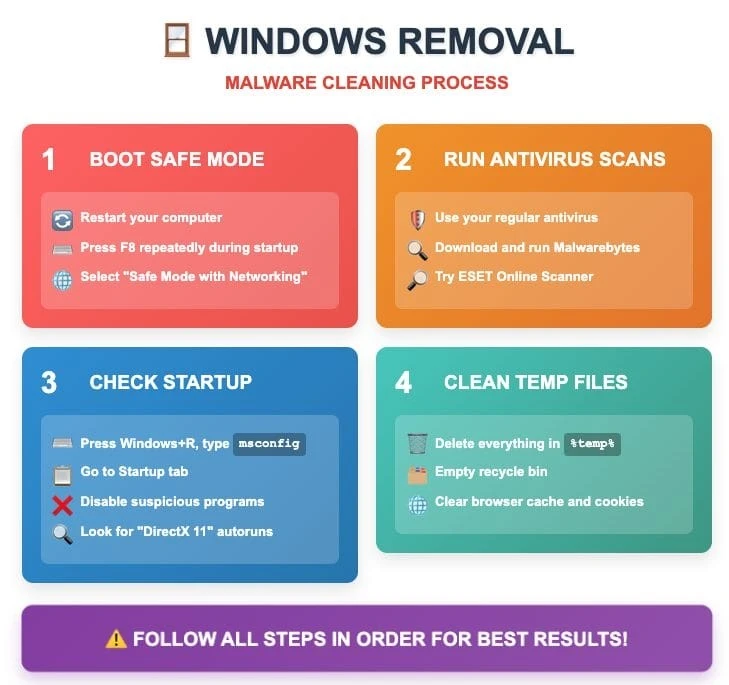
Windows systems require particularly thorough cleaning due to the nature of the integration of clipboard malware with the operating system. Start by booting your computer into "Safe Mode" to prevent the malware's defense mechanisms from activating. Many clipboard hooks prescribe themselves as system services or autorun programs to ensure their constant presence on the system.
Use multiple antivirus programs for comprehensive scanning. Different antiviruses specialize in detecting different types of malware, so running a scan with your main antivirus, as well as utilities like Malwarebytes and ESET's online scanner, will give you a more reliable result. Pay special attention to checking temporary directories, where clipboard malware components are often hidden.
Look for specific indicators described in cybersecurity research. One such infection has been spotted as part of the All-Radio 4.27 Portable malicious package. When this package is installed, a DLL file named d3dx11_31.dll is downloaded to the Windows Temp folder and a "DirectX 11" startup entry is created to run that DLL every time the user logs in. Check the list of startup programs for a "DirectX 11" entry and remove it if found. The execution pattern of the malware is predictable: the specified DLL will be run using the rundll32.exe rundll32 command C:\Users[username]\AppData\Local\Temp\d3dx11_31.dll,includes_func_runnded. You can find this command prompt in the list of active processes or in startup entries.
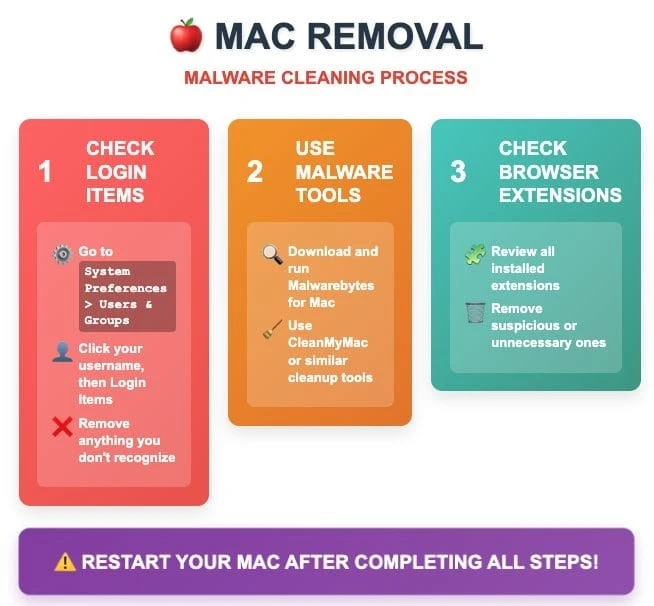
Mac System Restore
Mac users are also not immune to clipboard-related threats. Check the Login Items section of System Preferences (under Users & Groups) for programs you don't recognize. Clipboard malware on Mac is often disguised as legitimate system utilities or productivity apps. Check your installed browser extensions carefully, especially if you're using Chrome with cryptocurrency wallet extensions. Uninstall any extensions that you didn't install or that ask for permissions to access the clipboard.
Registry Wipe and Deep System Check (for Windows)
Advanced Windows users can check the startup keys in the system registry for suspicious entries. Note: Be extremely careful when editing the registry, as incorrect changes can cause the system to malfunction. Always back up the registry before making any changes! Press Windows+R, type regedit. Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. Look for entries you don't recognize. Delete suspicious entries (after making a backup!).
Advanced Clipboard Hijacking Strategies
Modern security when dealing with cryptocurrencies requires an understanding of both the technical aspects of clipboard attacks and the broader context of the threats that users face.
Hardware solutions for maximum security
Hardware wallets (or cold wallets) offer the most robust level of protection against clipboard attacks. This is because they display addresses on their own built-in screens, which makes it impossible to attempt address spoofing. Hardware wallets are considered the best solution for storing cryptocurrencies safely. The physical separation between your cryptographic keys and the devices connected to the internet creates a so-called "air gap" that clipboard malware is unable to overcome.
For those who are forced to use software wallets, it is recommended to consider the option of using a dedicated computer exclusively for conducting cryptocurrency transactions. Such a computer should remain offline most of the time, connecting to the network only when absolutely necessary to perform transactions, and should never be used for normal web surfing, checking email, or downloading third-party software.
Innovations in browser-level protection
Some modern browsers are starting to implement features aimed at protecting the clipboard. For example, the Opera web browser (version 84 and later) has a "Paste-Protection" feature that tracks any last-minute changes to the inserted information before insertion. This is a significant step in the evolution of browser security, although it is worth noting that even when using such a browser, which can prevent cryptocurrency theft, most users will not notice the very fact of intercepting the clipboard until it is too late.
Secure transactions with QR codes
The use of QR codes provides excellent protection against clipboard hijacking, as the QR codes themselves cannot be changed by malware running on your device. Whenever possible, always prioritize scanning a QR code over manually entering an address or copying and pasting.
Conclusion: Vigilance Is Your Greatest Ally
The most important security practice is to carefully verify the recipient's address. Even if you used copy and paste, always double-check the address after pasting, as clipboard interception malware may have replaced it with the scammer's address. This verification phase is your last and most reliable line of defense against clipboard attacks.
Remember that the world of cryptocurrencies is constantly evolving, and so are the threats. As the market for digital assets grows, it is not uncommon to see a commensurate increase in their illegal use. Maintaining awareness of new threats and adhering to digital hygiene practices is an ongoing process, not a one-time tweak. The security of your cryptocurrency savings is directly dependent on understanding these threats and integrated protection strategies. The combination of technical protection, safe habits, and constant vigilance provides the best defense against sophisticated clipboard attacks faced by today's cryptocurrency users.




celese Haha, classic! First they screwed over the players, then the license turned out to be fake, and now they’re trying to undo everything. A total circus. Yeah, everything will just get bought. They’ll pay whoever they need in Curaçao and get a new license. Money rules everything, especially in this industry.



Mangarin4ik The section about how casinos fire VPNs is a gun. I've never thought about WebRTC and the time zone. Author, thank you, you may have just saved my next deposit.





































Way too long to read
Malwarebytes + Kaspersky + offline download is my battle setup.
People, never, hear, NEVER open emails with the subject "Important crypto update". My wife almost opened the fake Ledger and followed the link. I barely pumped out the laptop
Every newcomer should not be explained "how to open a wallet", but "how not to be a sucker on the clipboard". A new level of education.
I don't use this
Sometimes it is necessary to copy and often